
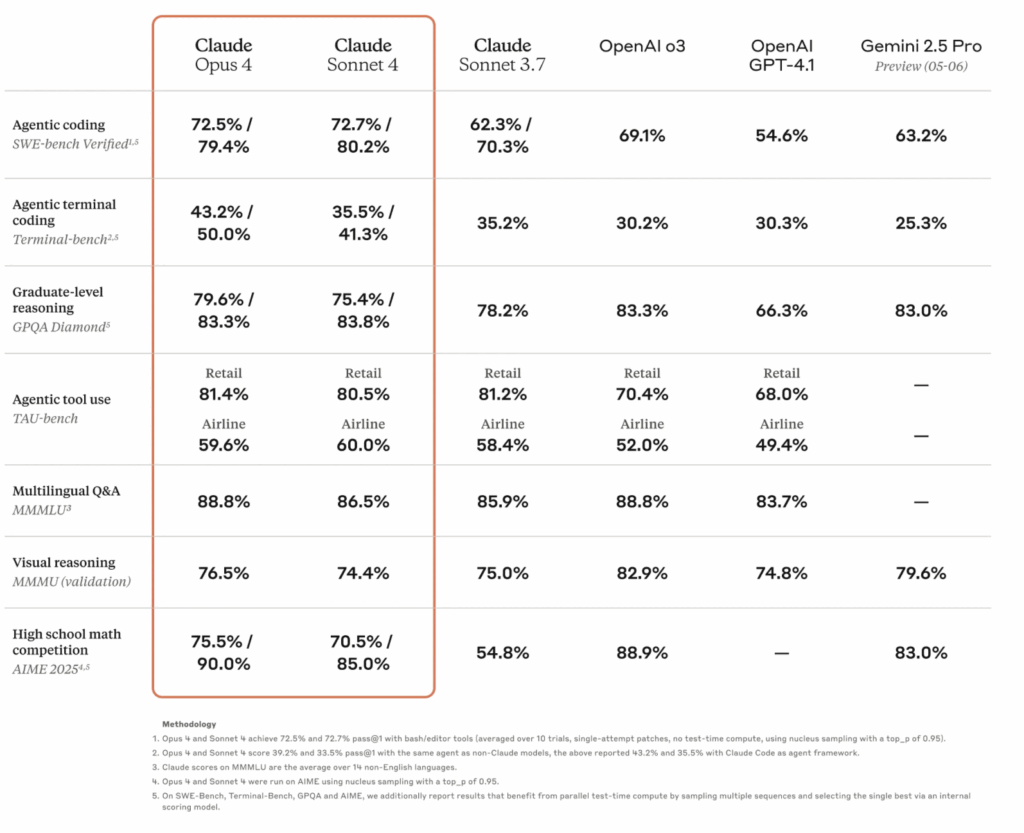
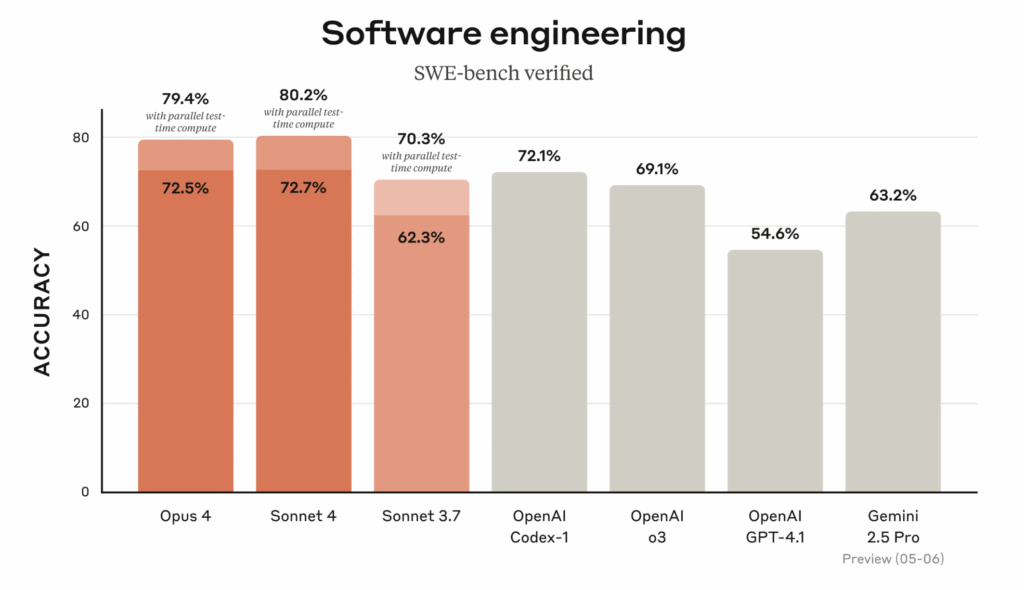
The recent release of Claude 4 (Opus 4 and Sonnet 4) brings significant improvements to AI-assisted coding, with Anthropic’s benchmarks showing substantial gains across multiple programming tasks. More importantly for security-conscious engineers, these improvements represent meaningful progress in reducing the attack surface created by AI-generated code vulnerabilities.
That made me and others think about reducing the threats for vibecoding. I wrote about the risks and threats here.
Impact: Lovable’s Production Data
The coding platform Lovable provides concrete evidence of Claude 4’s improvements in production environments. Their deployment data shows:
- 25% reduction in syntax errors across all generated code
- 40% improvement in generation speed
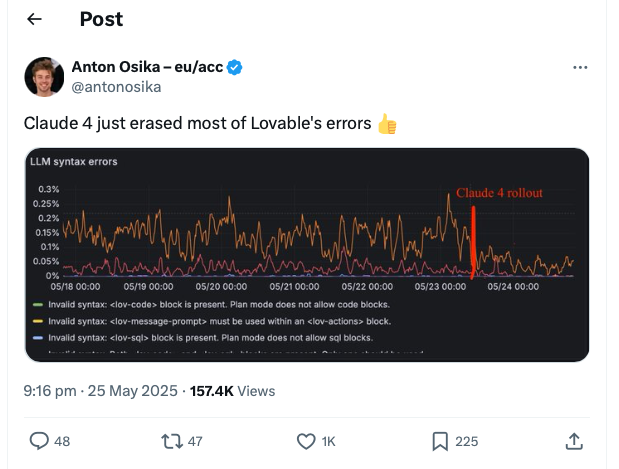
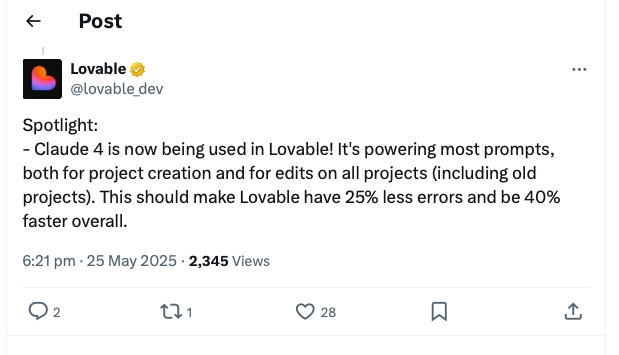
This real-world validation is particularly significant because it demonstrates improvements in the types of errors that often serve as entry points for security vulnerabilities.
Security Implications: Vibecoding Risk Mitigation
While Claude 4’s syntax error reduction doesn’t directly address semantic security issues like slopsquatting (e.g., malicious packages mimicking “huggingface-cli”), every improvement in code quality reduces the overall attack surface.
Recommendations for Security Teams
Given these improvements, security teams should:
- Code Reviews. Ask experienced developers in the field to review your vibed code.
- Never blindly trust AI-suggested packages. Always verify their existence and reputation on official repositories before installation.
- Use lower temperature settings in AI models to reduce randomness to improve accuracy.
- Ask the AI model to verify its own outputs for hallucinations.
- Cross-check outputs against a known list of valid packages or maintain detailed Software Bills of Materials (SBOMs) to quickly identify unauthorized or unexpected dependencies.
- Use RAG or fine-tuning: Retrieval-Augmented Generation (RAG) and supervised fine-tuning with real package data can reduce hallucinations.
- Test all AI-generated code in isolated environments before incorporating it into production codebases.
- Enhance developer training about the risks of AI-hallucinated dependencies.
- Implement dependency management tools like Dependabot (GitHub Security) or OWASP Dependency-Check to identify suspicious or newly published packages.
- Integrate automated security scanning tools like OWASP ZAP, Snyk, or SonarQube.
Conclusion
Claude 4’s documented improvements represent meaningful progress in AI-assisted development security. While not a silver bullet for vibecoding vulnerabilities, the 25% reduction in syntax errors and improved accuracy create a more defensible development environment. Security teams should view this as an opportunity to refine their review processes while maintaining rigorous security standards.
The key takeaway for security professionals: the fundamental need for security-conscious development practices remains unchanged.
Leave a Reply